Latest version: 4.3.x
Webhooks (Splunk)
Setup alerts from Lenses.io to Splunk via a Webhook to send to a Splunk HTTP Event Collector (HEC) connection.
Set up
1. Visit Admin → Connections and click New connection
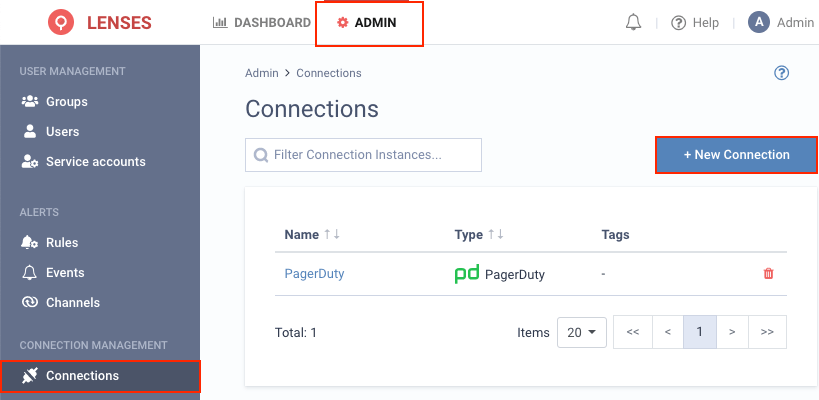
2. Select Webhook (Note: Use webhook for alerts, and for SIEM - audit events the native Splunk connection )
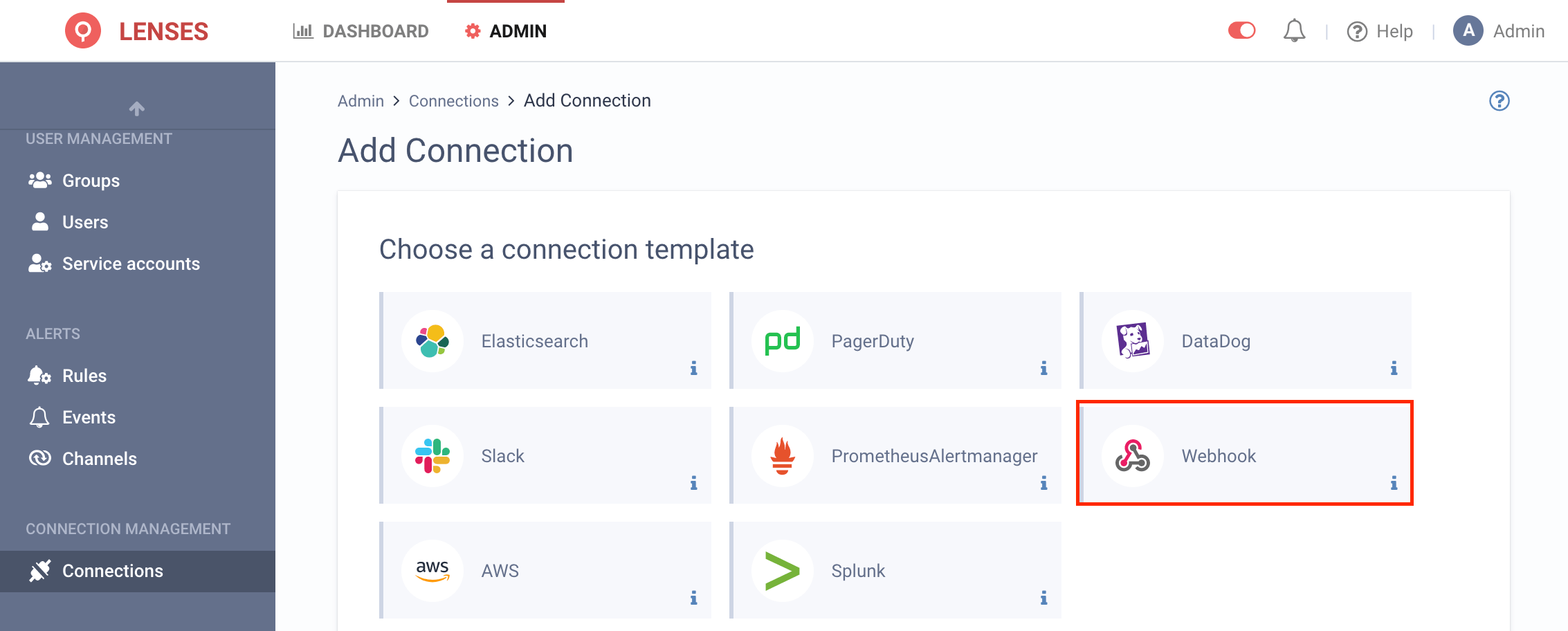
3. Provide a name and configuration
Provide a name for the Connection, such as SplunkWebhook
Enter the DNS or IP of your Splunk instance configured with a configured HTTP Event Collector listener. This should be without a path (ie. not including /services/collector for example)
Enter the port of the HTTP Event Collector (Splunk default: 8088).
Enable SSL if necessary.
Credentials are not required at this stage. The HTTP Event Collector Token will be provided in next step.
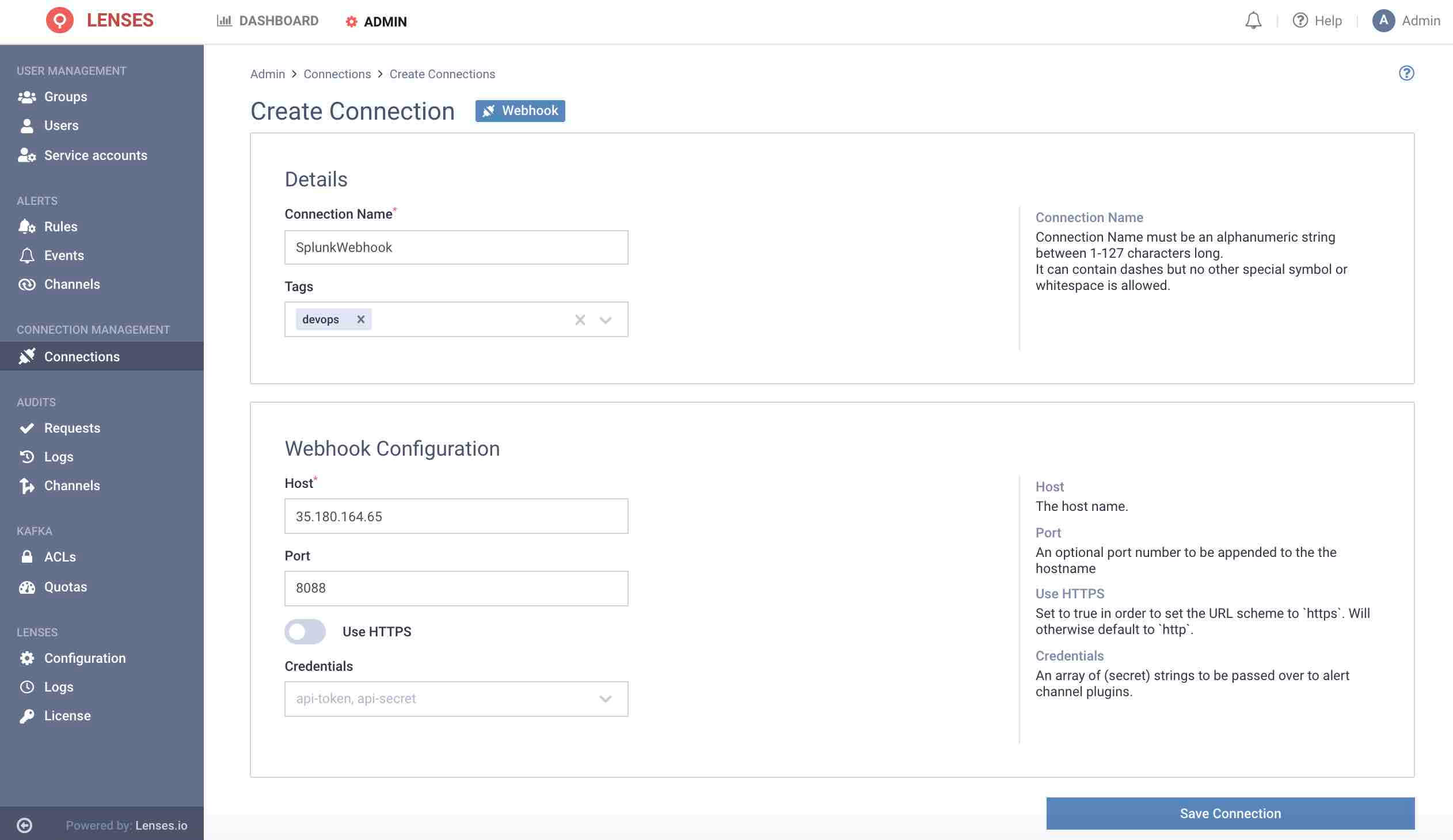
Add channel
Next add one or multiple target Splunk webhook channels.
1. Visit Admin → Channels and click Webhook
2. Setup the configuration options
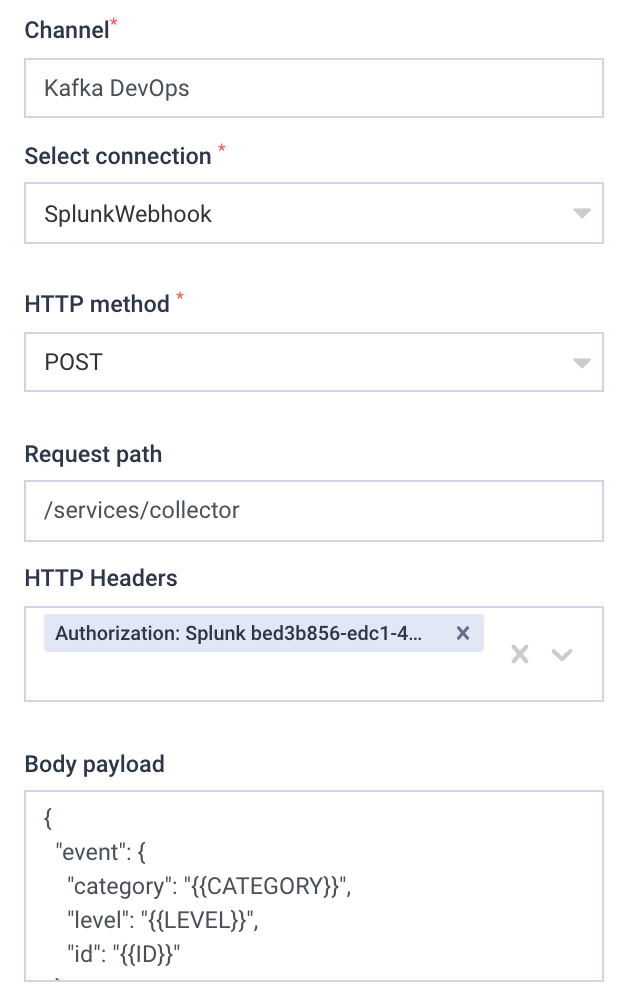
For example the above will create the Kafka DevOps channel, that is using the Webhook connection.
The Splunk Connection created in the previous step is selected as the Connection.
Enter a header declaring the Splunk HEC Token. The format must be:
Authorization: Splunk <<HEC TOKEN>>
For the Request path, enter the exact value:
/services/collector
The body payload must include a valid JSON object for Splunk to accept.
The alert payload must be held in an event object within the JSON. Such as:
{
"event": {
"category": "{{CATEGORY}}",
"level": "{{LEVEL}}",
"id": "{{ID}}"
}
}
See webhooks section for full details about available variables.
The event will appear like the following in Splunk:
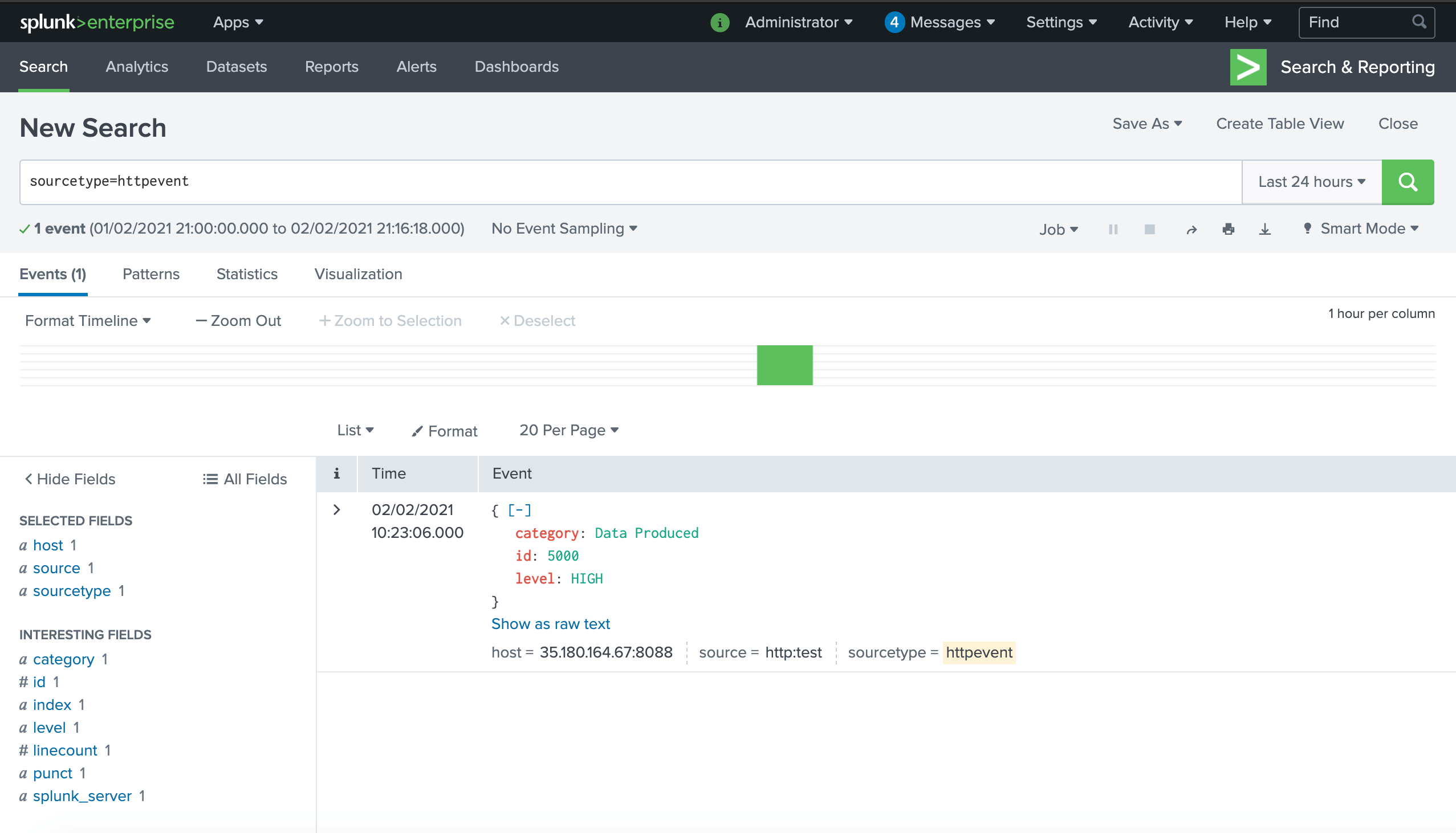
Test sending an alert before saving via a cURL command
curl -v -k PROTOCOL://YOUR_ SPLUNK_HOST:8088/services/collector -H "Authorization: Splunk YOUR_TOKEN" -d '{ "event": { "category": "{{CATEGORY}}", "level": "{{LEVEL}}", "id": "{{ID}}" } }'
An example
If for example you create a rule to send Apache Kafka Broker monitoring notifications to Splunk, the moment a Broker goes offline, an HTTP POST will be sent to Splunk via the Splunk HTTP Event Collector. This can then be also be analysed in Splunk ITSI.
Additional info
Users with the alert permission can create alert rules .
